Apple’s Webkit, Firefox, and now Chrome have all announced current or upcoming changes in the way their browser handle third-party cookies in order to provider strong tracking protections. This post explores the details of the upcoming tracking protections.
What are Third-Party Cookies? Link to heading
In any interaction on the web, there are two first-party entities: the browser requesting content, and the primary content location as specified by the URL bar. For instance, if I’m browsing in Firefox and access https://xkcd.com, the first parties in this interaction are Firefox and the xkcd.com host. All other entities involved in this exchange are considered to be a “third-party”. When it comes to cookies, those cookies that are associated with the xkcd.com domain are the only first-party cookies in the transaction.
In most cases, the web site I visit also serves content from other domains. For instance, when I visit https://slashdot.org, I get image resources loaded from https://cdn-social.janrain.com. These resources are served up with a cloudflare cookie (which my browser rightfully attached to subsequent requests), that uniquely identifies a user. While this particular example’s _cfduid cookie is fairly benign, there are many third-party resources that much more aggressively track user data.
Long Live the Cookies! Link to heading
Now here’s where the story starts to get interesting. Since a cookie is a client-side persistence mechanism, it costs web sites practically nothing to keep them around indefinitely. And so they do - tracking cookies often have expiries ranging years into the future. Remember the mostly benign _cfduid cookie? It instructs your browser to keep it around for an entire year.
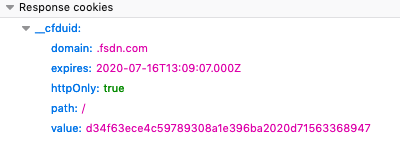
So, end-users wind up picking up cookies from all sorts of places, and the browser keeps the cookies around (practically) forever. The results:
- Bloated request/responses with lots of extra cookies
- Advertisers have the ability to track user activity indefinitely
Not good.
Browsers Fight Back Link to heading
In response to the tracking cookie problem, combined with growing privacy concerns on the internet, a number of standards have been introduced to change the way browsers handle third-party cookies. These include:
- Webkit’s Intelligent Tracking Protection (ITP), first introduced in 2017, currently at version 2.2.
- Mozilla’s Enhanced Tracking Protection (ETP), which became the default behavior in June of 2019.
- Chrome’s SameSite cookie standard. See this blog for an excellent explanation.
While the nuances of each of these implementations is beyond the scope of this post, the idea behind all of them is to give users more control over third part cookies and to provide stronger defaults in the blocking and disposal of these cookies.
Collateral Damage Link to heading
If you’re a consumer, rejoice! Thanks to the efforts of browser maintainers, your internet is becoming a safer, slightly less creepy place. However, if you’re a web developer, this can spell trouble. For instance, an SPA using OpenID’s Web Message Response Mode may no longer be able to silently authenticate using cookies.
The implications: any applications previously relying on background interactions with cookies to manage state (such as login status) on third-party sites, now have issues. Further discussion to come soon!